Security
We make sure that your RaspiNail is secure and reliable. Some of those tips are took from Raspiblitz config:
Table of contents
- Enabling the Uncomplicated Firewall
- fail2ban
- Increase your open files limit
- Disable Bluetooh
- Disable WLAN
The RaspiNail will be visible from the internet and therefore needs to be secured against attacks using various methods.
Enabling the Uncomplicated Firewall
A firewall controls what traffic is permitted and closes possible security holes. Only SSH and the Electrum server are reachable from the outside. Bitcoin Core and LND are using Tor and don’t need incoming ports.
The following steps need admin privileges and must be executed with the user “admin”.
$ sudo apt install ufw
$ sudo su
$ ufw default deny incoming
$ ufw default allow outgoing
$ ufw allow 22 comment 'allow SSH'
$ ufw allow 50002 comment 'allow Electrum SSL'
$ ufw enable
y
$ systemctl enable ufw
$ ufw status
> Status: active
>
> To Action From
> -- ------ ----
> 22 ALLOW Anywhere # allow SSH
> 50002 ALLOW Anywhere # allow Electrum SSL
> 22 (v6) ALLOW Anywhere (v6) # allow SSH
> 50002 (v6) ALLOW Anywhere (v6) # allow Electrum SSL
> ...
$ exit
🔍 more: UFW Essentials
💡 If you find yourself locked out by mistake, you can connect keyboard and screen to your Pi to log in locally and fix these settings (especially for the SSH port 22).
fail2ban
The SSH login to the Pi must be especially protected. Additional steps should be taken to prevent an attacker to just try out all possible passwords.
The first measure is to install “fail2ban”, a service that cuts off any system with five failed login attempts for ten minutes. This makes a brute-force attack unfeasible, as it would simply take too long.
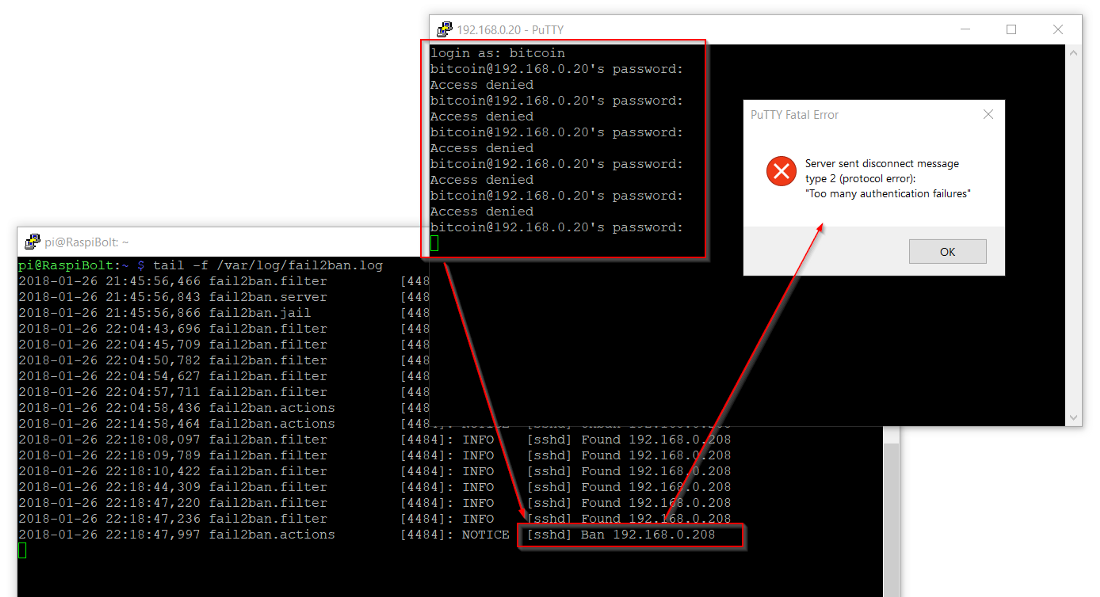 Me locking myself out by entering wrong passwords
Me locking myself out by entering wrong passwords
$ sudo apt install fail2ban
The initial configuration should be fine as it is enabled for SSH by default.
🔍 more: customize fail2ban configuration
Increase your open files limit
In case your RaspiNail is swamped with internet requests (honest or malicious due to a DDoS attack), you will quickly encounter the can't accept connection: too many open files error. This is due to a limit on open files (representing individual tcp connections) that is set too low.
Edit the following three files, add the additional line(s) right before the end comment, save and exit.
$ sudo nano /etc/security/limits.conf
* soft nofile 128000
* hard nofile 128000
root soft nofile 128000
root hard nofile 128000
$ sudo nano /etc/pam.d/common-session
session required pam_limits.so
$ sudo nano /etc/pam.d/common-session-noninteractive
session required pam_limits.so
Reboot the system:
$ sudo reboot
Disable Bluetooh
- As we are not using Bluetooth on the node, it is more secure to just disable it. Add those lines to the file
/boot/config.txt:$ sudo nano /boot/config.txt# RaspiNail - Disable bluetooth dtoverlay=disable-bt - Then proceed to disable its associated services:
$ sudo systemctl disable hciuart.service $ sudo systemctl disable bluetooth.service - Then proceed to remove bluetooth packages:
$ sudo apt remove -y --purge pi-bluetooth bluez $ sudo apt-get autoremove -y
Disable WLAN
Only if you are not using WLAN on the node. It is more secure to just disable it:
$ sudo systemctl disable wpa_supplicant.service
$ sudo ifconfig wlan0 down
Next: Privacy »